Spoofed Email Spams
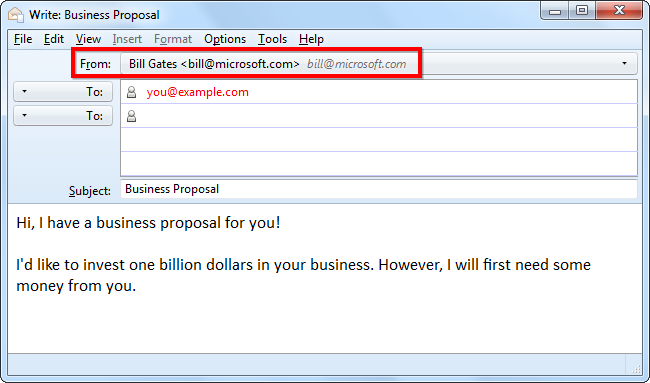
Since we continue to see increased cases of spoofed email spams, we need to better understand how this email fraud happens and what we can do about it although our options as email users are limited as you will soon find out.
Email spoofing is an email appearing to come from you, sent to people who recognize your email address. This criminal act usually happens when a malicious computer program collects our email address as well as those of our contacts and takes over the mail server such as Yahoo or Google Mail to send spoofed email spams without ever taking over our email account through stolen or guessed passwords. These email spam engines will often scan a user's address book, web cache and files to collect email addresses which is very difficult to prevent. As mentioned, these computer worms are capable of sending bulk emails while taking advantage of SMTP mail server weaknesses and not because email account owners were negligent. Although there are some email authentication systems such as DomainKeys Identified Mail (DKIM) which provides a method for validating a domain name identity that is associated with a message through cryptographic authentication, there are still plenty of spoofed email spams originating from mail servers which have implemented DKIM. Therefore, below are some recommendations to deal with spoofed email spams as much as possible regardless of whether we are on the sending or receiving end of the spoofed emails:
- Open separate email accounts for personal, catch-all and business use. Use a catch all email account for newsletters and other online registrations which can be used by spammers to collect and spam emails to collected addresses. A catch-all email account will protect your personal or business emails from being stolen and subsequently used for spoofed email spamming.
- Create unusual user names for the personal and business accounts because spammers often send emails to lists of common names at popular mail servers such as Yahoo. You're less likely to get spams if your user names are not easy to guess. Do not use your real name in the email address either such as JohnDoe@yahoo.com.
- Avoid giving away your email address to just anyone and any site and ask your friends and family members to also be careful about sharing your personal and business email accounts with others. Sometimes, it’s not worth sharing the email address with merchants for just a mere discount unless you use your catch-all email address.
- Change your email address if it is receiving a high volume of spam emails or used to send spoofed email spams.
- Delete unnecessary email sitting in the inbox.
- Delete unnecessary contacts sitting in the contact list.
- As mentioned, changing passwords doesn't help with spoofed email spams but as a good practice change it often to protect your account in case an intruder has taken over your account. Select unique and hard to guess passwords by selecting a mix of upper and lower case letters, numbers and special characters such as $, #, ! etc.
- Change Your Account Recovery Information. As you know, some accounts require secret questions and answers to allow for a password reset. Confirm your alternate email address associated with your account as well as any phone numbers. Also, remove all credit card and other personal information which can be used by a hacker to get access to your account.
- Check your email account settings to make sure it is not being forwarded to another account just in case your account was hacked into.
- Back up the contact list frequently by downloading or exporting it to a file which can then be imported into a new email account if necessary.
- Avoid duplication of contacts and emails stored in multiple systems.
- Avoid email forwarding to other accounts to avoid email duplication.
- Don’t reply back or forward spams and never click the links within the spoofed email spams. Delete them immediately.
- Update your anti-virus and anti spyware software periodically and run a scan weekly or when suspecting the presence of a malicious program or noticing a computer malfunction and slow performance.
- Don’t leave accounts logged in or agree to remember the login credentials. Although it might take a few extra seconds to enter your ID and pass code each time you want to use your account, it is safer to leave the account locked when it is not in use even when you walk away for a short while.
- When you notice or are notified that your email address is spoofed to send email spams, notify your contacts that you are not spamming them and ask them to ignore any solicitations from emails appearing to come from you to buy something online. Ask then to not reply, forward or click any links within.
- And lastly, you need to move on with your life when this happens. I know it’s devastating to find out that your personal or business email was used to send Viagra ads to the world but it is not your fault and most people know these days that the mail servers are vulnerable to email spoofing and spams because emails are not authenticated to detect and prevent spoofed emails.
Visit Identity Management Institute for education, training, and certification.






